Today I'm configuring the Remote - SSH extension VS Code under windows.
My configurations are mostly located in WSL2 folders. So I simply want to reuse directly the ~/.ssh/config file and rsa key files (with 400 permission) in ~/keys.
But it's not working. And I got the following "Permission too open" error when connecting to the remote linux server.
Env:
when using ssh to connect to remote linux server (eg. with VisualStudio Code ), it is easy to set access right of the file to 400 with a simple chmod 400 command, but in windows, it's not the same. With default config, we may have the following error.
Reason:
- windows is using different ways to manage user rights of files as linux.
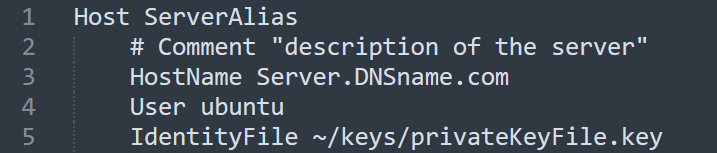
- the config of Remote SSH extension uses the same format as .ssh/config, but in the identify file path, it does not work well with spaces in the file path which is common in windows.
Solution:
- Put those keys files into a windows folder without spaces / special chars in the path and file name ( D:\keys\keyfile.key as an example)
- Change properties of the key file, and leave only necessary permission.
for example the default permission of the file is as following:
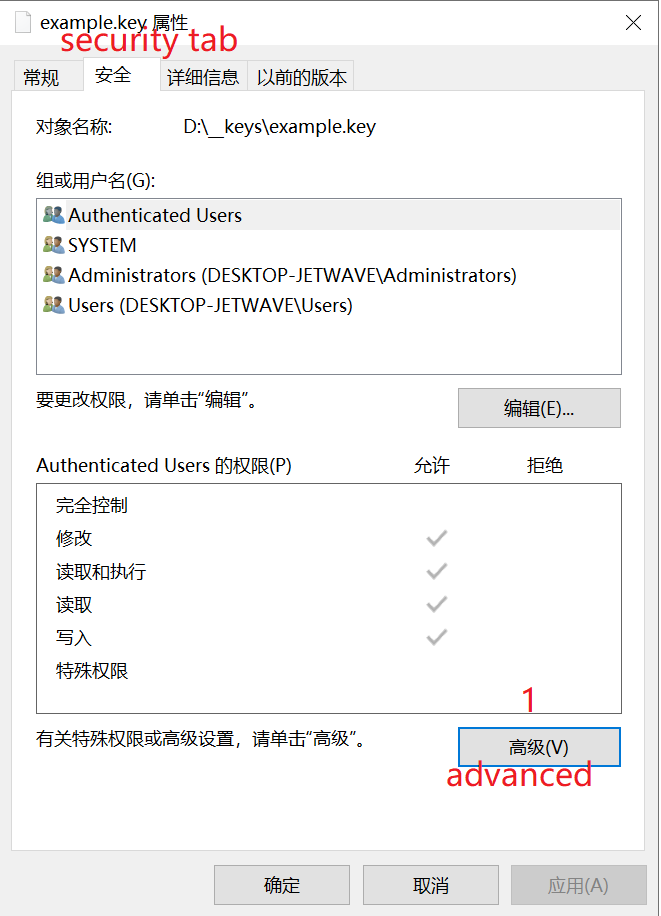
click on advanced button
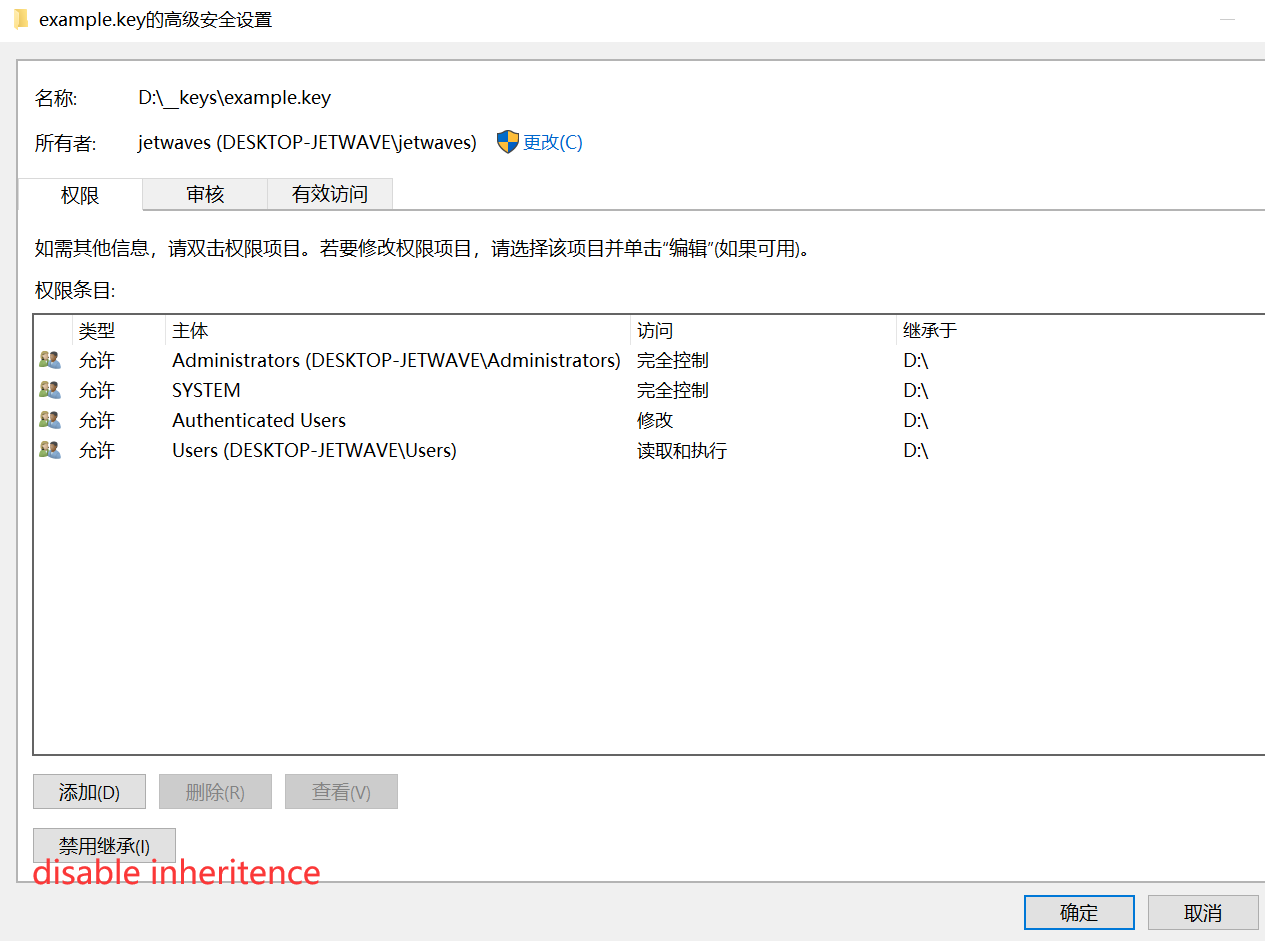
click on "disable inheritance", then you'll be able to modify permissions for each user and roles.
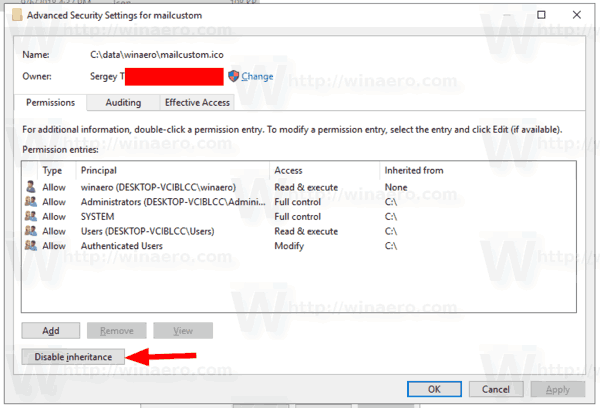
and then the tricky part: windows manage permission with roles but not specific users by default. so you need to ADD proper permission of your current user and then remove permission of other users/roles to make the permission clean.
click on Add button:
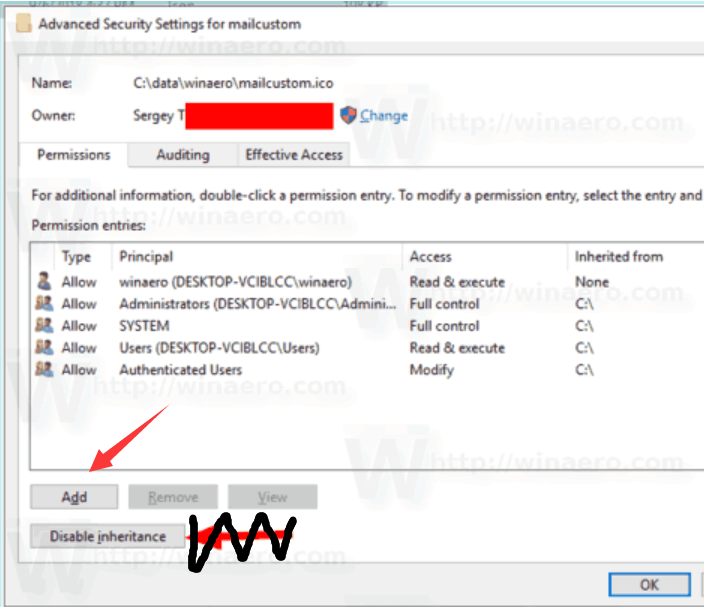
in the next windows, click on change/ add owner of the object(file),
in the select user popup, enter your current user name, and click on "Check Names", the full owner name (with user group) will appear in the text area. then click on OK.
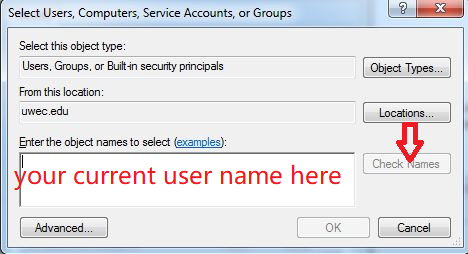
and then back to the following window, remote any user other then the user you've just added.

finally, configure the permission of your current user as "allow read"
you'll have the permission of the key file as clean as following:
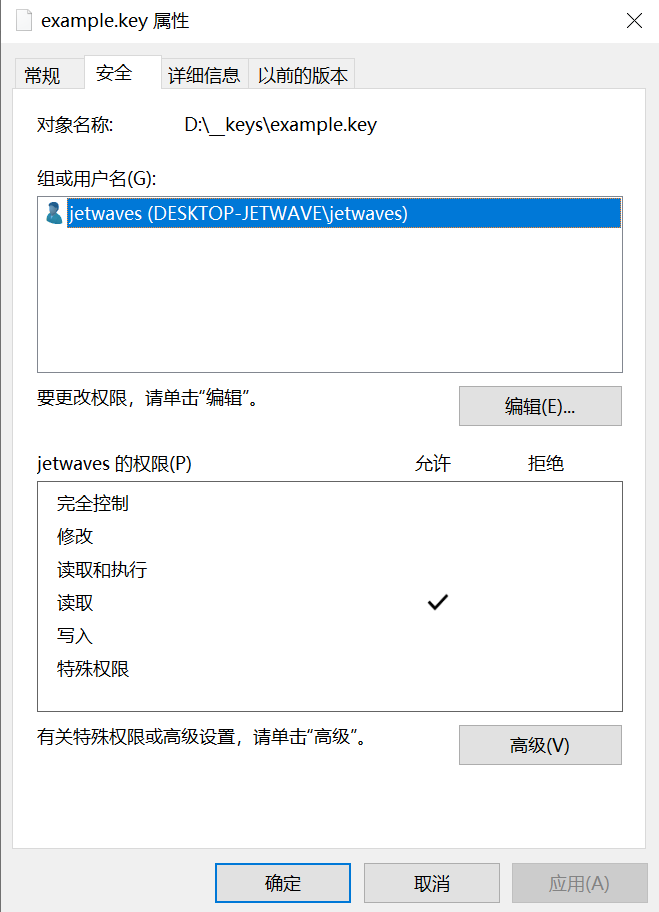
This will be functional for the ssh.